Hey! I'm Roman, CTO at Techvice. Sometimes I do mobile apps reverse engineering to access APIs and reproduce queries in Python or NodeJS code. This is necessary to create a data scraper. In one of the recent scraped apps I noticed traces of using IBM MobileFirst.
IBM MobileFirst (or IBM Mobile Foundation) is a platform for developing, optimizing, integrating and managing secure mobile applications.
Disclaimer
-
I won't mention here the name of the application.
-
The IBM site documentation notes that this protection doesn’t provide unbreakable encryption, but provides a basic level of obfuscation.
Application Analysis
Firstly, I tried to intercept traffic between the mobile application and the server using mitmproxy. But I got an error because the application uses SSL pinning.
To disable SSL pinning, I used the Frida utility. Here’s one of the examples Frida's scripts to bypass SSL pinning - https://codeshare.frida.re/@pcipolloni/universal-android-ssl-pinning-bypass-with-frida/.
I tried to use frida scripts we created for applications we explored before, but nothing worked. This application probably has a custom SSL pinning implementation for which my past practice doesn’t work.
Application Decompilation
For decompiling Android applications I used JADX.
techvice@MacBook-Pro-techvice some_app % jadx -d ./source_code ./some_app.apk
INFO - loading ...
INFO - processing ...
ERROR - finished with errors, count: 25
At the output, JADX gave us 2 directories: resources and sources. Let's take a look inside the source.
techvice@MacBook-Pro-techvice some_app % ls -la source_code/sources
total 0
drwxr-xr-x 18 techvice staff 576 Jun 27 15:18 .
drwxr-xr-x 5 techvice staff 160 Jun 27 15:19 ..
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 a
drwxr-xr-x 4 techvice staff 128 Jun 27 15:18 android
drwxr-xr-x 5 techvice staff 160 Jun 27 15:18 androidx
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 b
drwxr-xr-x 33 techvice staff 1056 Jun 27 15:18 c
drwxr-xr-x 19 techvice staff 608 Jun 27 15:18 com
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 cordova
drwxr-xr-x 23 techvice staff 736 Jun 27 15:18 d
drwxr-xr-x 4 techvice staff 128 Jun 27 15:18 de
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 defpackage
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 e
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 im
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 net
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 nl
drwxr-xr-x 5 techvice staff 160 Jun 27 15:18 org
drwxr-xr-x 3 techvice staff 96 Jun 27 15:18 uk
In the sources directory of the decompiled application, there is a Cordova directory. Well, we know what we are dealing with now.
Applications built on Cordova are regular web applications that run on the Chromium engine. JS, CSS and HTML files required for the application work located in the `resources/assets/www` directory. I open this directory and see…
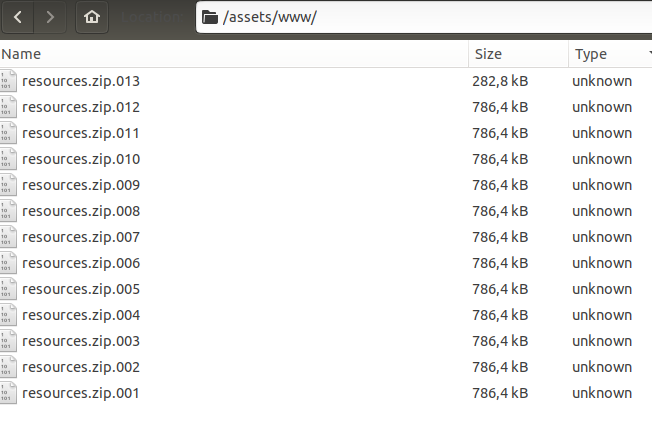
Surprise! Instead of the expected HTML, CSS and JS files, I saw a zip archive split into several parts.
Of course, I tried to unpack it, but, as expected, I got an error that the archiver was unable to do this.
Getting Source Code
Firstly I looked for the encryption key, tried to research how the encryption/decryption algorithm works. A few hours later it struck me…

Previously I said that Cordova applications are regular web applications running on the Chromium engine. But Chromium can't decompress and decrypt zip archives! So, before the application starts, this archive should be unpacked somewhere.
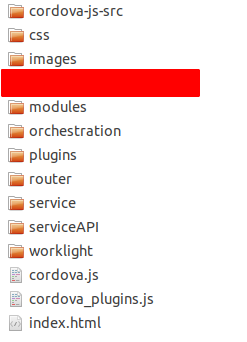
I launched the app on the Android Emulator. Using SSH I connected to the emulator shell and executed a couple of bash commands like find . -name index.html . After a few minutes, I managed to find a place on the file system where the encrypted zip archive is unpacked.
This is what the source code looks like.
Final Thoughts
I clicked on index.html, which opened in Chrome browser. Then at the Network tab in Chrome Dev Tools (to open press F12) I found all the requests that the application makes to the server.

